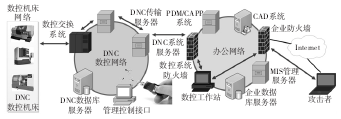
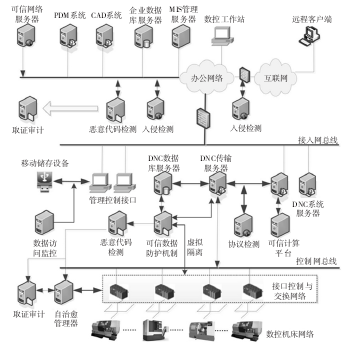
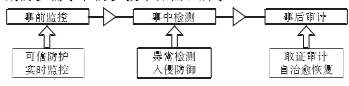
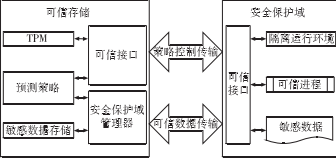
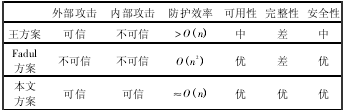
0 Preface The intrinsic security vulnerabilities of the CNC system and the openness after networking make the information security threats it faces continue to expand. CNC system is the "brain" of CNC machine tools. The core technology of high-end CNC system is basically monopolized by the industrialized countries, and the CNC system has uncontrollable loopholes, backdoors and other security risks. At the same time, information security attacks on the control system continue to occur. Once the numerical control system is destroyed, it will cause the NC machine tool and even the entire production line to stop, causing serious losses to the company. Therefore, research on the theory and technology of information security protection for CNC machine tools is of great significance for ensuring the stable operation of industrial infrastructure. The U.S. Department of Energy National SCADA Testbed Program (NSTB) issued a roadmap for a protective control system. The guidance document for the protective control system developed by the European Network and Information Security Agency (ENSIA) was also released in 2011. Domestic Wang Qikui proposed a digital processing network information security protection plan, and deployed CNC processing network boundary isolation equipment and CNC system terminal protection equipment to ensure the security of CNC network. Wang Jian proposed the DNC CNC network security protection architecture and deployed firewalls to filter data between office LANs and DNC NCs. However, this solution lacks effective protection against internal information leakage. Yu Liye proposed a defense-in-depth defense solution for information security in industrial control systems, adopting an access control mechanism for boundary isolation and intrusion detection, and lacking systematic coordination protection. Trusted computing and self-healing are considered as important methods to solve the intrinsic safety of the control system. Fadul applies the trusted computing theory to the protection of SCADA systems in smart grids. Wu Jiangjiang proposed a non-authorized protection of data based on a virtualized isolated data trusted storage system. Wei Zhanqi proposed a reliable data encapsulation scheme based on reversible extension. At present, the research of trusted network theory and technology is mainly in the office network of general information systems or numerical control systems, and has not yet been applied to a complete numerical control system. Zhang Hao studied the network survivability theory based on self-healing theory for power system, but did not study the complete system architecture model. Kirsch studied survivable SCADA systems through intrusion tolerance strategies, but its strategy does not apply to stateful application servers. This paper establishes a comprehensive network information security protection program for CNC machine tools, establishes a systemic information security coordination protection technology, and organically combines existing information security protection technologies to achieve better protection effects while maintaining system orderliness. 1. CNC machine network system architecture and security threats In order to increase the level of informationization and comprehensive automation of CNC companies and achieve integration of management and control, modern CNC systems are increasingly interconnected with corporate networks, and computer-aided design and manufacturing (CAD) and product data management systems (PDM) are used to improve processing efficiency. Accuracy. Intelligent components such as common protocols (such as TCP/IP protocols) and general operating systems are constantly used for industrial data exchange and processing. The interconnection of CNC machine tools with office networks and even the Internet has led to more information security threats for CNC systems. CNC machine automation network structure and security threats are shown in Figure 1. Figure 1 CNC machine tool automation network structure and security threats In Figure 1, the CNC machine tool network is connected to the DNC CNC network via a data exchange system through interfaces such as RS232 and serial ports, and then interconnected with the office automation system. The double arrow indicates the path of the security threat. As can be seen from Figure 1, the security threats mainly come from external attacks and internal attacks. The external attack is mainly the vulnerability of the attacker to scan the target network system through the external Internet, find the attack point, and conduct continuous attacks (such as advanced persistent threats). Internal attacks include malicious data leakage, virus transmission through mobile devices, and so on. Attack targets include manipulating the control system, interrupting the processing process, affecting product quality, and stealing corporate data. 2, CNC machine tool automation network comprehensive protection technology The proposed comprehensive network protection technology for CNC machine tools mainly includes the system architecture and core protection technologies. 2.1 Security Protection Architecture Based on the structure of Fig. 1, a coordinated and systematic security protection system architecture for CNC machine tool automation network system is presented, as shown in Fig. 2. The network security protection system of CNC system in Figure 2 covers three aspects of office network security protection, DNC CNC network and CNC machine equipment network security protection. In the office network protection, basic protection measures such as firewalls, intrusion detection, and malicious code detection are deployed. At the same time, a trusted network management server is deployed to filter malicious nodes and improve network immunity. For DNC NC networks, deploy a trusted computing platform on the DNC server to ensure that the operational control system is trusted; deploy the protocol intrusion detection server to filter non-compliant system control flows; deploy trusted data protection mechanisms in DNC data transmission and data read and write To prevent unintended access; Deploy the data access monitoring module on the management control interface to prevent malicious intrusion of mobile devices. For field device protection, the self-healing manager is deployed mainly at the interface control and switching layer to prevent equipment operation failures from affecting production. Each stage of protection connects to the forensic audit server for auditing when necessary. Figure 2 CNC Network Security Comprehensive Protection Architecture In order to achieve comprehensive synergy protection, various protection technologies need to be integrated. Taking the time as the axis, an event-driven protection scheme is proposed. The event lifecycle protection requirements and protection technologies are shown in Figure 3. Figure 3 Schematic diagram of the event life cycle protection Combining with Fig. 2 and Fig. 3, before the occurrence of security incidents, real-time monitoring and trusted platform protection methods are adopted in the DNC numerical control network; in the office network, trusted networks and reliable early warning methods are adopted. When a security incident occurs, active access control and anomaly detection methods are used for internal attacks. For external attacks, use intrusion prevention, malicious code defense and other methods. After a serious security incident occurs, it starts a self-healing and fault-tolerant recovery mechanism for the CNC machine tool network, establishes the threat sources and threat methods in the forensic audits of various networks, and uses upgrade patches, intrusion prevention and other methods to prevent the recurrence of the incident. With trusted protection technology and self-healing as the core protection technology, it integrates basic data and system protection technologies, and dynamically builds an integrated information security protection mechanism for NC systems based on the event life cycle. 2.2 Trusted Protection Technology First, deploy the trusted computing platform on the DNC system server. The DNC system server is a key node that connects the office network and CNC machine tools. It issues instructions from the office network to the CNC machine tool network and uploads the NC machine tool data and status information to the office network. The credibility of its operating platform is crucial. Trusted computing platform takes the Trusted Computing Module (TPM) as the core and password and verification technology as the trust chain to ensure the trusted and secure computing platform. The trusted computing platform is mainly used for pre-monitoring, authenticating legal systems and ensuring that the platform is controllable. Reject unexpected control of the device layer after a security incident. Second, the trusted data protection mechanism is deployed on the DNC digital network to protect the core data of the CNC system, as shown in Figure 4. Figure 4 Trusted Data Protection Mechanism A VPN-like communication isolation environment is dynamically built on the control network bus to ensure that the device control data is not leaked. Combine trusted computing and virtualization technologies to build a virtual machine system on a DNC CNC network and establish a secure data protection domain (SPDSecureProtection Do-main). By binding sensitive data in a secure domain, the data is expected to be protected against DNC ​​data. The access request carries out security verification and policy control to prevent untrusted processes from reading and writing data to data and transferring them to untrusted areas, thus realizing data leakage protection. Pass the untrusted process to the malicious code detection server to check for malicious intrusion. The trusted virtual data protection mechanism is mainly used for advance monitoring, security isolation, in-service intrusion detection, and post-event auditing. Third, deploy trusted web servers on the office network. In the dynamic operation, the trusted node has a certain degree of intelligence, and its trust is related to the behavior. The trust theory is an effective method to solve the behavior credence. According to the historical performance of the node to determine the trust value, the node larger than the trusted threshold can participate in the service. To isolate malicious nodes. The trusted network is mainly used for in-flight detection, combining intrusion prevention and malicious code defense to provide evidence for auditing. Based on the above three aspects, a trusted protection model of the numerical control system is established. With traditional data protection and system protection technologies, data security and system security of CNC systems are realized. 2.3 Data and System Security Basic data security protection technologies mainly include traditional data isolation technologies (such as access control and firewalls), data leakage prevention technologies, and data security storage technologies. The data isolation device is deployed between the external interface network of the CNC system, the access network bus, and the control network bus, and serves as a basic protection measure for pre-event monitoring and event detection. The data security protection mainly cooperates with the trusted data protection mechanism, and sets the data control function of the mobile device to the running data and stores it on the mobile device. Once accessing the system or encountering abnormal access, the data access monitoring server is actively connected and the access control mechanism is started. Sensitive data in the DNC data server cooperates with the information protection domain manager for secure storage. Basic protection technologies for system operation include protocol detection, intrusion detection, and malicious code detection. The system security protection mainly cooperates with the credible protection and self-healing mechanism. Deploy an intrusion detection/defense system on the office network and DNC CNC network. Real-time monitoring of system operating status, analysis of proprietary industrial communication protocols, and exploration of intrusion clues for post-event auditing. The process of rejection by trusted protection is judged by the intrusion detection system and a defense response is made. At the same time, collect malicious attack evidence for post-event auditing. When the attack threat affects the availability of CNC machine tools, a self-healing fault-tolerance recovery mechanism is initiated. 2.4 Self healing and fault tolerance The principle of the self-healing mechanism is that in the event of an attack, the system accepts risks and feedback adjustments to make the system within the scope of the health work, so as to achieve immunity to attacks. Establish a self-healing manager on the CNC machine network interface and exchange system. By monitoring the system's operating status and behavior to determine whether the system's change is in an acceptable range, and then implement the appropriate strategy. Detect abnormal operation behavior of CNC system, monitor the abstraction of collected values, correlate with CNC system's functional attributes (such as availability), and determine based on the constraint evaluation values ​​of various components of CNC system, determine whether the CNC system is operating within an acceptable range, beyond a certain limit. When component/network thresholds are set, system abnormality alarms are performed. At the same time, the self-healing response mechanism is started, a defense recovery strategy and an inference evolution mechanism are generated according to the goals that the current system state needs to reach, recovery mechanisms are used to recover the violation of system constraints, and feedback is applied to the operating system. Fault recovery is mainly to ensure that the system can continue to provide services in the event of a disaster, or can quickly restore the attacked system to normal conditions. Redundancy technology is the most basic fault-tolerant recovery technology. Redundant machine tools are deployed in the CNC machine tool network, and software redundancy modules are deployed on the network interface and switching network of CNC machine tools. At the same time start the self-test technology, find the fault location, shield or isolate the faulty part. The process information of system change and fault location is recorded in the form of logs and stored in the audit server for auditing when necessary. 2. 5 Comprehensive protection mechanism The above step-by-step model was integrated into the NC system event life cycle. Mainly integrates the trusted protection technology into the real-time monitoring beforehand to realize the trusted access control. It integrates the self-healing mechanism into fault recovery afterwards. Combines the data security protection technology with the trusted mechanism to protect the data security in the event cycle. System security technology is integrated into the incident detection, with a trusted mechanism for post-mortem audit. 3, analysis of comprehensive protection scheme of numerical control system safety 3. 1 Functional Analysis of Protection Schemes The proposed solution can address the following types of attacks. Malicious Code Attacks: Attacks on malicious code using hardware, software, and protocol vulnerabilities of CNC network systems. In the integrated protection system, the malicious code detection mechanism deployed in the external network and internal network can detect malicious attacks. Trusted access monitoring can discover the invasion of mobile storage devices. The integrity-based access control requirements of the trusted virtual protection domain can block malicious Code attacks and alerts or initiate self-healing fixes. Unauthorized access: Initial isolation is performed by a security isolation device. The trusted data protection mechanism deny access and submits to the audit server. Information leakage: It is mainly the leakage of internal network information. It can rely on trusted data isolation environment, sensitive data security protection domain, and data read/write authentication. According to the operation log, conduct an audit. Denial-of-service attacks: Attacks on system servers, DNC transport servers, and interface switches in the DNC numerical control network do not work properly or buffer overflows. In the comprehensive protection scheme, the monitoring of access traffic is mainly detected through the protocol, and the non-trusted access request is blocked by the trusted computing platform. Once the CNC machine tool fails, the redundant mechanism in the self-healing mechanism is started to ensure availability, and the self-check mechanism is used to recover the fault. Protection Plan Synergy: When faced with various attacks, comprehensive utilization of the credible protection, data and system based protection, self-healing protection, and coordinated protection of the CNC system. (1) Time coordination of protection programs. Trusted protection is used for advance monitoring and implements trusted access control. Self-healing mechanism is used for fault recovery afterwards. Basic data security protection cooperates with trusted data protection and is used for active data access control in the event. Basic system security protection cooperates with trusted protection. The intrusion detection is performed on the trusted protection rejection process and the evidence of the attack is collected for post-event auditing. When the attack threatens the availability of the CNC system, a self-healing fault-tolerance recovery mechanism is initiated. (2) Space coordination of protection programmes. The proposed scheme makes full use of the numerical network architecture to deploy protection technologies with different resource attributes. The CNC machine tool network requires high real-time performance. It uses a trusted virtual domain isolation mechanism to prevent unauthorized access, and deploys intrusion prevention mechanisms for CNC machine tools in CNC networks. . Once it breaks through all protective measures, it starts a self-healing mechanism to isolate and repair damaged equipment. In the DNC numerical control network, the trusted platform and intrusion prevention monitoring platform are deployed to ensure the security of the core control system. Deployment of complex trusted networks, intrusion detection, malicious code detection and other measures in the office network to ensure the reliability of the peripheral network. 3. 2 Protection Program Performance Analysis The proposed defense scheme is a typical defense-in-depth solution. It mainly increases the interface mechanisms (I) of the trusted protection module (T), the self-healing module (S), and the IPS and malicious code detection modules. The time complexity is respectively f. (t(T)), f(t(S)), f(t(I)), f is a function of time. The pre-monitoring phase is mainly the continuous monitoring of the trusted protection module and the time of the proposed protection plan (P). The complexity is f(t(P)) = f(t(T)) = O(n) where n is the number of trusted modules deployed. In the middle of the detection phase, it includes credible protection detection, data and system protection detection, and self-healing recovery. The computation complexity of the trusted network is O(n12), n1 is the number of transmission nodes, the event complexity of the trusted data protection mechanism is O(n) + O(1), and O(1) is occasionally accessed by external mobile devices. The monitoring time, self-healing return to O(1), and the complexity of data and system protection O(n), so the detection phase f(t(P)) = f(t(T)) + f(t) (S) ) + f( t( I) ) = O(n12) +2O(n) + 2O(1). The time complexity of post-audit forensics is O(1). The space complexity is mainly to increase the trusted management server, self-healing management server and corresponding data storage server, and the space complexity is 3O(n). 3. 3 Comparative analysis Compared with Wang Qikui's proposed CNC protection network protection scheme (abbreviated as Wang scheme), the proposed scheme has added a trusted protection, self-healing, and system coordination protection module. Wang's plan mainly uses processing network boundary isolation equipment and terminal protection equipment to cooperate with auditing and protection protocols to protect the CNC system. In the aspect of anti-attack, the Kings scheme has a good effect on external attacks, but has weaker protection against malicious internal leaks. In terms of efficiency, the King scheme requires deeper inspection of communication content, fine-grained access control, and host intrusion prevention, all requiring pattern matching and computation. The time complexity is between O(n) and O(n2), where n is the number of calculated entities. In terms of protection effectiveness, in-depth inspection of field devices will reduce usability, there will be no mention of protection measures against integrity damage, and delays in dealing with security attacks will be lagging behind. Compared with Fadul's proposed smart grid credible protection scheme, the proposed scheme is more comprehensive. The Fadul solution uses a reputation-based trust management system to mitigate attacks against future smart grid infrastructure vulnerabilities that are deployed in smart grid communications support protection systems. In terms of anti-attack, the Fadul solution is weak in anti-burst attacks because of delay in reputation feedback. In terms of efficiency, reputation calculation and trust management require multi-domain network communities to participate in iterative calculations. The time complexity is close to O(n2), the space complexity is mn, m is the length of entity history vector, and n is the number of entities. In the aspect of protection effect, the reputation-based malicious attack immune mechanism and the reasonable allocation mechanism of communication bandwidth make it have better security and appropriate usability, but lack of integrity protection. The above analysis results are listed in Table 1. The protection effect is represented by three levels of attribute values: “excellentâ€, “mediumâ€, “poor†and “poor†indicate that the corresponding attributes are not mentioned or have poor results. There is a certain effect, slightly less than "medium." Anti-attack effects are divided into 2 states: Trusted and Untrusted. Efficiency is expressed in terms of time complexity. The results shown in Table 1 are the relative performance of this method as the current standard, and the superiority of the proposed scheme can be inferred. Table 1 Comparison of protection schemes 3.4 Example Analysis Taking the Advanced Persistent Threat (APT) attack as an example, the effectiveness of the proposed comprehensive protection scheme is analyzed. APT attacks can flexibly combine multiple new attack methods, penetrate the target for a long time, and perform attacks at specific times. The typical APT attack process for numerical control systems is divided into five phases. 1 Collect intelligence. Use social engineering to collect and lock specific CNC machine tools. 2 Break through the defense. Utilize server vulnerabilities, website malware, phishing software, and mobile client vulnerabilities to break into the office network host and gain access to the compromised host. 3 establish strongholds, horizontal penetration. Establish a channel for controlling the server to the victim host and obtain system authority, horizontally detect the structure of the office network system and the DNC network and data access rules, invade more hosts, and avoid being discovered. 4 Attack DNC system server. Simulate normal nodes, connect DNC ​​system server and DNC transmission server, use server vulnerability, and obtain system code execution permission. 5 Complete the attack. Modify or destroy control data, resulting in damage or downtime of CNC machine tools, and evacuation strategies such as trail destruction. The protection of the comprehensive protection plan mentioned is mainly divided into 4 stages: In the first stage, attack the office network host. The firewall, intrusion detection, and malicious code detection mechanism deployed in the office network can block part of the intrusion behavior. The deployed trusted network can isolate untrusted hosts based on their long-term historical performance. And submit the forensic audit module. The second phase, horizontal penetration attacks. Penetration within the office network is isolated from the above-mentioned intrusion detection and trusted network. The penetration of DNC numerical control network adopts protocol detection, data access monitoring, and trusted data protection mechanism to monitor abnormal data flow, block malicious node's reading and writing of data information in CNC network and intercept control information, and provide early warning. In the third stage, the DNC system server is attacked. The trusted computing platform deployed on the server passes the integrity authentication, rejects the malicious node's unintended control of the operating system, determines data tampering, and alerts in real time; the associated trusted data protection mechanism on the DNC transport server blocks malicious instructions. Transmission, and submit the malicious code detection server to further detect defenses and conduct forensic audits. In the fourth stage, malicious behavior bypasses the trusted platform and attacks the device. Initiate a virtual isolation mechanism to isolate the compromised CNC machine tool and control the scope of the attack. Start the self-healing mechanism and provide continuous service through a non-faulty redundant machine tool. At the same time, start the self-checking technology, shield or isolate the faulty components, and repair and audit them in time. This maximizes the elimination of APT attacks. According to the basic structure of Figure 2, the simulation environment was set up, the protection scheme was deployed, the APT attack method was simulated, and various penetration techniques were used to invade the DNC CNC network 20 times to read and destroy the DNC control file as the target. The experimental results show that the attack is effectively blocked. The first phase attack blocking probability (blocked attacks account for the total number of attacks) is 40%, the second phase detection probability is 30%, and the last 30% are in the third phase. Blocked. In summary, the proposed comprehensive protection scheme has a good protective effect against APT attacks. 4 Conclusion This paper proposes a comprehensive protection scheme of automatic network system security for numerically-controlled machine tools, which effectively solves the problems of information security protection for CNC machine tools and has better cooperation and effectiveness than previous solutions. The program can form a complete process protection, and self-contained system, have a good protective effect on APT. Due to the inherent security features of the trusted protection technology and self-healing, the solution can be deployed in heterogeneous heterogeneous CNC systems. Grinder , Sander or Polisher at some point they are synonym. They are widely used in industrial grinding sanding polishing processes. They are passive to carry out the force imposing by our Force Control System, active contact flange, or Constant Force Actuator. So our force control system is an integral part for the whole grinding sanding polishing system. Cheap grinding grinder,cheap sanding sander,cheap polishing polisher DARU Technology (Suzhou) Co., Ltd. , https://www.szforcecontrolsystem.com